X rules of a safe CEX by Vitalik Buterin

Vitalik Buterin shared his ideas on why modern CEX are not secure and how to fix it
The FTX bankruptcy raised broader concerns among investors and regulators alike. The former lost money, while the latter got another ground to intensify regulatory control over the crypto market. FTX collapse affected not only retail investors, but also institutional organizations, such as pension funds (e.g. Canada's Ontario Teachers' Pension Plan). So such questions, as "Who bears blame?", "Why did this happen?" and "How to prevent such things in the future?" get back on track.
Vitalik Buterin shared the consequences of another CEX revolution in his blog. He together with Coinbase CTO Balaji Srinivasan and other colleagues from Coinbase, Kraken, and Binance exchanges discussed how crypto exchanges could rebuild their lost trust.
Proof of deposits, combined with the user's ability to control the assets
The Mt. Gox and FTX bankruptcy cases prove that there is no point in looking for solutions or relying solely on traditional approaches that might work for banks or insurance companies. The realm of virtual assets follows its own rules that do not recognize any centralization or external influence. Neither state licenses and certificates, audits of corporate governance, nor the reputation of top managers work effectively for DeFi and blockchain technology. Pushing old, conservative regulatory methods into the world of digital assets and crypto banking is the same as demanding spaceships follow civil aviation rules.
Consequently, this sphere should adopt cryptographic methods and blockchain technologies to address its problems. Alternatively, exchanges can create and publicly provide cryptographic proofs that show that the funds they hold on-chain are enough to cover their liabilities to their users.
Another, even more ambitious, approach is to build an automated resource and financial management system that would prevent the withdrawal or misuse of investors’ funds without their consent. This would create a new, fairer consensus between the "evil" CEXes that pretend to be "good," and unpopular DEXes that can "be evil," but operate inefficiently and use vulnerable smart contracts and "leaky" protocols.
Balance lists and Merkle trees: Old-school proof-of-solvency
Exchanges made their first attempt to cryptographically prove that they were not cheating their investors back in 2011. Mt. Gox, the largest centralized exchange at the time, proved the availability of funds by sending a 424,242 BTC transaction to a pre-announced address.
In 2013, the crypto community started discussing how to solve another problem: the total size of customers' deposits is not less than the total amount of investors' deposits. If you prove that all user deposits equal X (the "proof of liabilities"), and confirm the ownership of private asset keys for X coins (the "proof of assets"), then you'll get a proof of solvency. Hence, CEXes can prove that they have enough funds to pay back to all their investors.
The easiest way to prove the size of funds is to publish a list of balances. This is a registry that contains the usernames and balances of their accounts. Each user can check his/her own balance and the total balance of the exchange. Of course, this violates privacy, so we need to change the scheme a little: publish a list of pairs containing only the hash and the balance. But, even this will leak some confidential information. Wishing to keep privacy, Vitalik suggests using Merkle tree techniques.
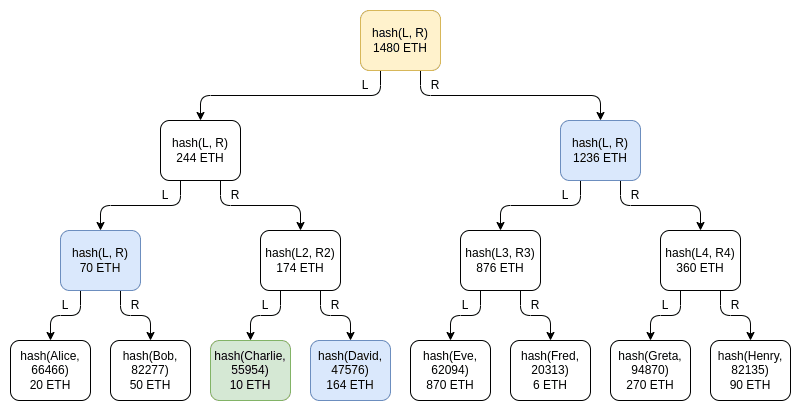
Merkle Tree example
Without going into the details of the scheme itself, we can see that it reduces privacy leakage to a minimum, but the privacy level will remain less than ideal and the balances of some users will be publicly available. There are better technologies, which we will discuss below.
Improving privacy and security with ZK-SNARK
ZK-SNARKs is a powerful zero-knowledge cryptographic protocol that provides privacy. The algorithm must ensure correct operation and correct response without violating user privacy. And therefore, we can certainly use ZK-SNARKs to improve privacy in proof-of-liabilities protocols.
The simplest thing we can do is to put all user deposits into the Merkle tree and use ZK-SNARK to prove that all balances in the tree are non-negative and equal to the claimed value. If we add a hash level for privacy, the Merkle branch given to each user will reveal nothing about the user's balance.
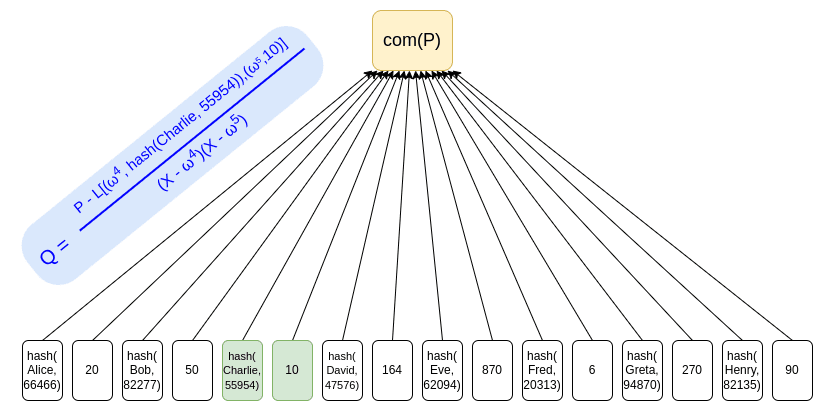
ZK-SNARK usage example
The root of this structure may even be published in the public domain. Such an implementation brings us closer to one of the ideas discussed in the article “Decentralized Society: Finding Web3' Soul”. According to its authors (including Vitalik Buterin), Web3 still lacks a soul or rather many souls connected by many links. This is supposed to be the backbone of Web3, which, in turn, will lay the foundation for an even more complex structure called a "decentralized society" (DeSoc). This society will be able to live completely autonomously without intermediaries like governments and corporations.
Proof of assets
The simplest version of proof of assets is the scheme we mentioned above. To prove that you hold X coins, you transfer X coins at a pre-agreed time in a transaction where the data field must state "these funds belong to a specific exchange". To avoid paying transaction fees, the transaction can be signed and sent off-chain.
However, there are certain difficulties associated with the confirmation of assets held in cold wallets, which can be addressed in several ways. An exchange can keep a few hot wallets with public addresses specifically for reporting to investors. At time X, the exchange transfers assets to public addresses, advises investors to confirm ownership, and then returns the assets to the cold wallets.
Later, public wallets can be reused for the same purpose, or you can use each address only once and never return to it again. This is by far the easiest option, although it adds certain risks and has limitations in keeping security at the highest level. Some exchanges already do something like this for auditing, but nothing prevents them from making it a fully automated procedure.
There may still be difficulties with proving the fiat assets that are held in the banking system. But this can also be addressed – the bank itself can attest to a certain amount of assets, or it can be verified and confirmed by independent auditors. Given that fiat currencies cannot be verified by cryptographic methods and blockchain technology, this is the best solution within that framework, and it's worth doing.
The same approach can be used to validate fiat collateral in non-digital assets against stablecoins.
Can we make CEXes non-custodial?
Suppose we want to go further: not just to prove that the exchange has enough funds to pay them back at the first users' request, but to prevent users' funds from stealing. For this purpose, we can use the Plasma technology.
Plasma works by splitting up (defragmenting) the balance into a set of individual "coins", where each coin gets an index and stays at a particular position in the Merkle tree of a Plasma block. To make a user-authorized transfer, transactions must be put into the correct position in the tree, whose root is published in the blockchain. CEX is not able to execute such a transaction, as the exchange has no rights to make certain transactions with other users' assets.
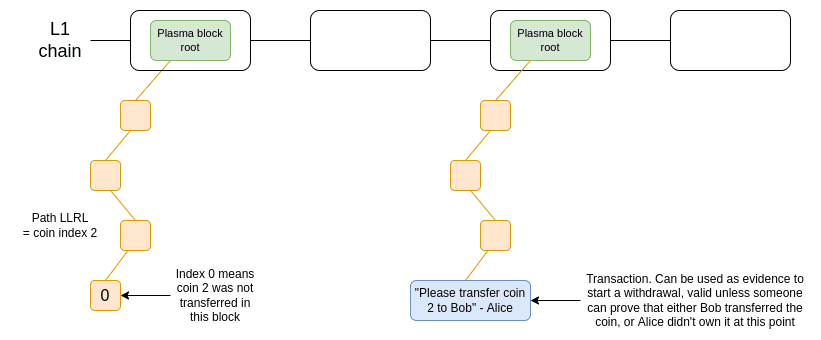
An example of Plasma technology. Coins are stored in a smart contract that enforces withdrawal rules of the Plasma protocol
A more modern version of the Plasma idea is Validium. This technology works similarly to ZK-rollup, except that the data is held off-chain. In this scheme, the "operator" (CEX) is unable to steal funds, though some funds may get stuck if the operator idles.
As it turns out, CEX and DEX are not the only operating formats for exchanges. There can be a whole range of other options, including various forms of hybrid centralization, where you gain some benefits like efficiency but still have a lot of cryptographic guardrails preventing the CEX from most forms of abuses and thefts.
Conclusions
In the short term, there are still two opposite "classes" of exchanges: custodial and non-custodial exchanges. Today, the latter category is simply DEXes, such as Uniswap. In the future, we may see cryptographically "constrained" CEXes, where user funds are stored in a kind of Validium smart contract. This will be the next level
The easiest way to improve the security of custodial exchanges is to add proof of reserve. The procedure should combine proof of assets and proof of liabilities.
In the long run, we will eventually come to the point where all exchanges will become non-custodial (DEX), and CEXes with their attempts to steal assets will become a thing of the past. The only thing left is to develop a user-friendly procedure to regain access to wallets, if you lost your password or private keys. But that's a whole different ball of wax…

