What is the "Red Pill Attack"?

ZenGo, a cryptocurrency wallet team, recently discovered a vulnerability within the Web3 transaction simulation of various popular asset storage solutions. The issue was promptly addressed by developers, with a comprehensive report on the matter published shortly after.
Before we delve into this vulnerability, it's indispensable to comprehend the fundamentals of transaction simulation. In the era preceding the advent of smart contracts, cryptocurrencies were confined to the realm of private transfers. In our contemporary digital landscape, however, they have seamlessly been incorporated into decentralized applications, the proliferation of which shows no signs of slowing down.
To instill confidence in the security of smart contracts, all principal wallets have adeptly integrated this innovative technology into their platforms. During the initiation of a transaction, a simulation is set into motion within a virtual environment, presenting the user with a forecast of the likely outcome from their interaction with the application, prior to their confirmation.
Typically, monetary losses can be attributed to malicious Web2 interfaces or fraudulent code. The former are designed with the sinister aim of coaxing assets out of smart contracts, while the latter cunningly coax victims into transferring tokens under an array of pretexts. This vulnerability in simulation has been a boon for fraudsters, offering them an effective means to craft their deceit.
The "Red Pill Attack"
At the heart of this issue is a pernicious code capable of identifying a simulation and projecting a positive outcome for the user. However, upon dispatch to the blockchain, it invariably fails to execute. The code for the attack employs specific indicators within the transaction, colloquially known in the Solidity programming language as "special variables".
These are engineered to display volatile information, such as fees, miner addresses, or block numbers. Such parameters become the eponymous "red pills", primarily because a multitude of developers tend to overlook security protocols and assign them constant values. This oversight has led to users being misguided via the interface of diverse wallets.
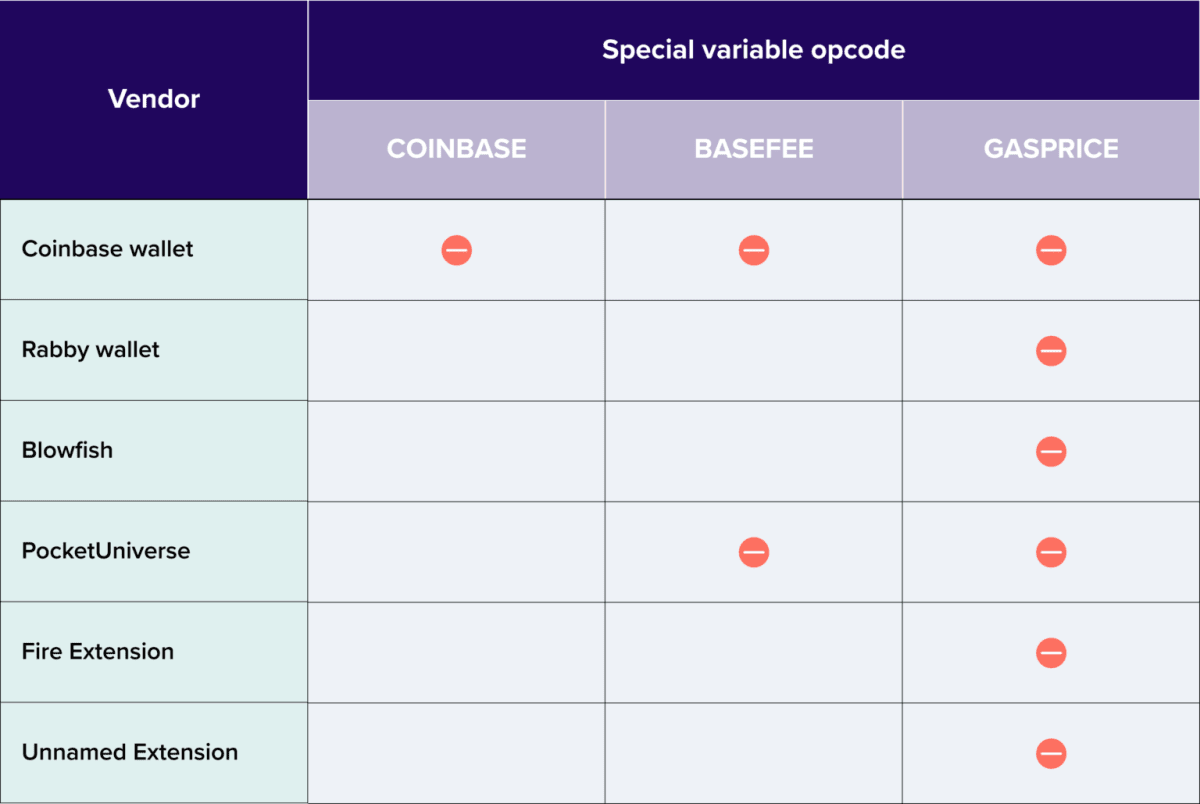
Vulnerable extensions, wallets, and simulation hosts. Source: официальный блог ZenGo.
To mitigate this, it is crucial to input precise values: either the miner of the latest block or a random number (representing the assumed fee). Fortunately, popular wallets swiftly addressed the vulnerability. Although a handful of developers are attempting to tackle the menace of fraudulent smart contracts with a personalized inbuilt Web3 firewall, transaction simulation remains an indispensable tool. Its key role in safeguarding novices from potential financial losses cannot be overstated, and it must invariably function with utmost precision.

